In today’s digital landscape, ensuring your organization’s systems are secure is paramount. Firewalls serve as the first line of defense, enabling organizations to control traffic and protect against unauthorized access. This article provides a step-by-step guide to setting up iptables firewall rules to meet specific business security requirements, including blocking unauthorized connections and securing network communications.
Scenario
You are a Network Security Engineer tasked with configuring firewall rules for a startup. The key objectives are:
- Block all incoming connections except from trusted sources.
- Enable secure communication while allowing specific protocols.
- Prevent insecure connections like HTTP traffic.
- Save firewall configurations to persist across reboots.
Objective-Based Firewall Rules
Requirements
- Block all incoming packets except from specific IPs:
- Allow traffic from
8.8.8.8and8.8.4.4only.
- Allow traffic from
- Enable ping (ICMP) both inbound and outbound.
- Block all outgoing HTTP (port 80) traffic and send an ICMP error message for such requests.
- Ensure firewall configurations persist after setup.
Step-by-Step Firewall Configuration
1. Default iptables Setup
Modern Linux systems use iptables as a powerful firewall management tool. Ensure that the default policy for the INPUT chain is set to DROP to block all incoming traffic not explicitly allowed.
sudo iptables -P INPUT DROP
2. Allow Trusted Incoming Connections
Add rules to accept connections only from Google Public DNS IPs (8.8.8.8 and 8.8.4.4):
sudo iptables -A INPUT -s 8.8.8.8 -j ACCEPT
sudo iptables -A INPUT -s 8.8.4.4 -j ACCEPT
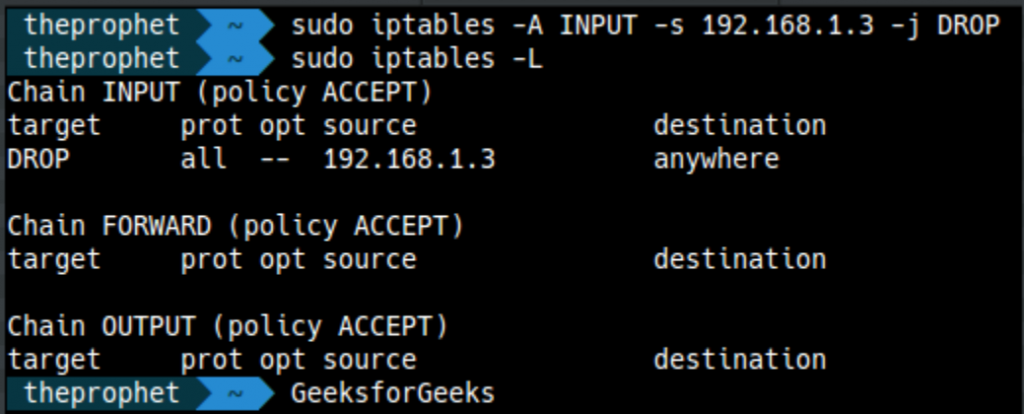
This ensures that only trusted sources can connect to your system.
3. Enable Ping (ICMP)
To allow diagnostic tools like ping, enable ICMP echo request and reply traffic:
# Allow incoming ping requests
sudo iptables -A INPUT -p icmp --icmp-type echo-request -j ACCEPT
# Allow outgoing ping replies
sudo iptables -A OUTPUT -p icmp --icmp-type echo-reply -j ACCEPT
4. Block Outgoing HTTP Traffic
To block all outgoing HTTP traffic on port 80 while sending an ICMP error message, add the following rule:
sudo iptables -A OUTPUT -p tcp --dport 80 -j REJECT --reject-with icmp-port-unreachable
This ensures that no insecure HTTP connections are established, improving the overall security posture.
5. Verify Firewall Rules
To verify that the rules have been applied correctly, use:
sudo iptables -L -v
This command lists all active rules along with packet counters and policies for each chain (INPUT, OUTPUT, etc.).
6. Save Firewall Rules
To ensure that the rules persist across system reboots, save the current configuration. If your system includes a script called save.sh, execute it:
sudo sh save.sh
Sample save.sh Script
If save.sh is not predefined, create it with the following content:
#!/bin/bash
iptables-save > /etc/iptables/rules.v4
if [ $? -eq 0 ]; then
echo "iptables rules saved successfully to /etc/iptables/rules.v4"
else
echo "Failed to save iptables rules. Please check permissions or paths."
exit 1
fi
Make the script executable:
chmod +x save.sh
Run it to save the rules persistently.
Example Configuration File (/etc/iptables/rules.v4)
Once saved, the rules should look like this in the configuration file:
*filter
:INPUT DROP [0:0]
:FORWARD ACCEPT [0:0]
:OUTPUT ACCEPT [0:0]
-A INPUT -s 8.8.8.8/32 -j ACCEPT
-A INPUT -s 8.8.4.4/32 -j ACCEPT
-A INPUT -p icmp --icmp-type echo-request -j ACCEPT
-A OUTPUT -p icmp --icmp-type echo-reply -j ACCEPT
-A OUTPUT -p tcp --dport 80 -j REJECT --reject-with icmp-port-unreachable
COMMIT
Testing and Validation
To ensure the configuration works as expected:
- Attempt to ping your system from allowed (
8.8.8.8,8.8.4.4) and disallowed IPs. - Test outgoing HTTP connections and confirm they are blocked.
- Check that ping requests and replies are functioning correctly.
Conclusion
Setting up firewalls with iptables is a fundamental aspect of securing your organization’s network. By carefully configuring and persisting firewall rules, you can block unauthorized connections, allow only approved traffic, and prevent insecure communication. The step-by-step guide and examples provided here should help you confidently implement a robust firewall configuration for your startup’s systems.
Pro Tip: Regularly review and audit your firewall rules to ensure compliance with evolving security policies and threats.

